What Is Key In Database Management System
Juapaving
Mar 19, 2025 · 7 min read
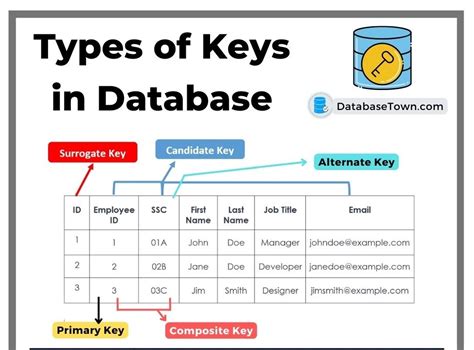
Table of Contents
What is Key in Database Management System? A Comprehensive Guide
A Database Management System (DBMS) is the backbone of any modern application that deals with structured data. Understanding the concept of keys within a DBMS is crucial for designing efficient, reliable, and scalable databases. Keys are fundamental for enforcing data integrity, ensuring uniqueness, and establishing relationships between different data entities. This comprehensive guide delves deep into the various types of keys in a DBMS, explaining their functionalities and importance in database design.
Understanding Keys in Database Management Systems
In simple terms, a key in a database is a unique identifier for a row (or record) within a table. It's a column or a combination of columns that uniquely identifies each record, preventing duplication and ensuring data consistency. Think of it as a social security number for a person – it uniquely identifies that individual within a larger population. Without keys, managing and querying data would become incredibly complex and error-prone.
The Importance of Keys
The significance of keys in database management cannot be overstated. They play several critical roles:
-
Data Integrity: Keys are essential for maintaining data integrity. They prevent the insertion of duplicate records, ensuring that each record is unique and accurately represents a single entity.
-
Efficient Data Retrieval: Keys drastically speed up data retrieval. Instead of scanning entire tables, the DBMS can use keys to quickly locate specific records, dramatically improving query performance.
-
Relationship Management: Keys are fundamental to establishing relationships between different tables in a relational database. They enable the linking of data from multiple tables, creating a cohesive and interconnected data model.
-
Data Normalization: Proper key usage is integral to database normalization, a process that organizes data to reduce redundancy and improve data integrity. Normalization relies heavily on identifying and utilizing appropriate keys.
-
Data Security and Access Control: Keys can be integrated into security mechanisms, enabling granular access control and restricting data access to authorized users only.
Types of Keys in a DBMS
There are several types of keys, each serving a specific purpose within the database schema:
1. Candidate Key
A candidate key is a minimal set of attributes (columns) that uniquely identifies each tuple (row) in a table. A table can have multiple candidate keys. For example, in a table of employees, both employee_id and social_security_number could be candidate keys, as they both uniquely identify each employee.
Characteristics of a Candidate Key:
- Uniqueness: Each value of the candidate key must be unique within the table.
- Minimality: No subset of the candidate key can uniquely identify tuples. Removing any attribute from a candidate key would violate uniqueness.
- Non-redundancy: A candidate key should not contain redundant attributes.
2. Primary Key
The primary key is selected from among the candidate keys. It is a single column or a combination of columns that uniquely identifies each row in a table. A table can only have one primary key. This key plays a vital role in maintaining data integrity and ensuring data consistency.
Characteristics of a Primary Key:
- Uniqueness: It must uniquely identify each row.
- Not NULL: The primary key column cannot contain NULL values.
- Non-redundancy: It should not contain redundant data.
3. Foreign Key
A foreign key is a column or a set of columns in one table that refers to the primary key of another table. Foreign keys establish relationships between tables, allowing data from different tables to be linked together. They are crucial for representing relationships between entities in a relational database.
Characteristics of a Foreign Key:
- References Primary Key: It must reference the primary key of another table (or itself, in the case of a self-referencing relationship).
- Enforces Referential Integrity: It ensures that values in the foreign key column exist in the referenced primary key column. This prevents orphaned records (records with foreign key values that do not correspond to any primary key values).
- NULL Values Allowed (Optional): In many cases, foreign keys can allow NULL values, signifying the absence of a relationship.
4. Super Key
A super key is any set of attributes that uniquely identifies each tuple in a table. A super key can include attributes that are not strictly necessary for uniqueness. A candidate key is a minimal super key – it contains only the essential attributes for uniqueness.
Characteristics of a Super Key:
- Uniqueness: Uniquely identifies each tuple.
- May contain redundant attributes: Unlike a candidate key, it can contain extra attributes beyond what's minimally required for uniqueness.
5. Alternate Key
An alternate key is any candidate key that is not selected as the primary key. A table can have multiple alternate keys if it possesses several candidate keys. These keys provide additional ways to uniquely identify rows within the table.
Characteristics of an Alternate Key:
- Candidate Key: Must be a candidate key.
- Not the Primary Key: It is a candidate key that was not chosen as the primary key.
6. Composite Key
A composite key is a primary key or a foreign key that consists of multiple columns. This is necessary when no single column can uniquely identify each row in a table.
Characteristics of a Composite Key:
- Multiple Columns: Composed of two or more columns.
- Unique Combination: The combination of values across all columns must be unique.
Practical Examples and Use Cases
Let's illustrate these concepts with some practical examples:
Example 1: Employees and Departments
Consider two tables: Employees and Departments.
-
Employees Table:
employee_id(INT, Primary Key)employee_name(VARCHAR)department_id(INT, Foreign Key referencing Departments.department_id)salary(DECIMAL)
-
Departments Table:
department_id(INT, Primary Key)department_name(VARCHAR)
Here, employee_id is the primary key in the Employees table, uniquely identifying each employee. department_id is a foreign key, linking each employee to their respective department in the Departments table. department_id in the Departments table is the primary key.
Example 2: Product Catalog
Imagine a product catalog with a table named Products.
- Products Table:
product_id(INT, Primary Key)product_name(VARCHAR)category_id(INT)manufacturer_id(INT)price(DECIMAL)
In this case, product_id is the primary key. However, you might consider a composite key using product_name and manufacturer_id if the product names aren't unique across all manufacturers.
Example 3: Orders and Order Items
Let's consider an e-commerce system with tables for orders and order items.
-
Orders Table:
order_id(INT, Primary Key)customer_id(INT, Foreign Key referencing Customers.customer_id)order_date(DATE)
-
Order_Items Table:
order_item_id(INT, Primary Key)order_id(INT, Foreign Key referencing Orders.order_id)product_id(INT, Foreign Key referencing Products.product_id)quantity(INT)
Here, both Orders and Order_Items tables have primary keys, and Order_Items uses foreign keys to link to both the Orders and Products tables. The relationship between Orders and Order_Items is a one-to-many relationship (one order can have multiple order items), which is managed through the foreign key order_id in the Order_Items table.
Advanced Key Concepts
Surrogate Keys
Surrogate keys are artificial keys that are generated automatically by the database system. They are not derived from any other attributes in the table. They are commonly used as primary keys when there is no natural candidate key that is suitable or when dealing with complex relationships. Benefits of using surrogate keys include simplifying key management, ensuring uniqueness even in the face of updates or modifications to underlying data and providing better performance in some query operations.
Natural Keys
Natural keys are keys that are already present in the table and represent some inherent attribute of the entity. For example, employee_id or social_security_number could be considered natural keys. While convenient, natural keys may present challenges such as potential changes over time or difficulty in ensuring uniqueness in certain contexts.
Conclusion
Keys are the fundamental building blocks of any relational database. Understanding the different types of keys – candidate keys, primary keys, foreign keys, super keys, alternate keys, and composite keys – is paramount for designing effective, efficient, and reliable database systems. Choosing the right key type for each scenario is critical for maintaining data integrity, streamlining data access, and facilitating robust relationships between data entities. Mastering these concepts is essential for any aspiring database administrator or application developer. By carefully selecting and implementing keys, you ensure that your database functions optimally and consistently delivers accurate, reliable information. Remember to always consider the potential implications of each key type and carefully analyze your data model to choose the most suitable solution for your specific requirements.
Latest Posts
Latest Posts
-
Least Common Multiple Of 6 5 And 7
Mar 19, 2025
-
What Is The Lcm Of 6 And 10
Mar 19, 2025
-
Least Common Multiple Of 14 And 24
Mar 19, 2025
-
When Dissolved In Water Acid Produce
Mar 19, 2025
-
How Many Hours Is 1500 Minutes
Mar 19, 2025
Related Post
Thank you for visiting our website which covers about What Is Key In Database Management System . We hope the information provided has been useful to you. Feel free to contact us if you have any questions or need further assistance. See you next time and don't miss to bookmark.
